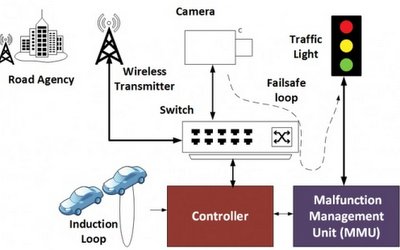
While it might sound like a plot line from the latest action blockbuster, the exposure of traffic signal systems to hacking is a real risk that needs to be addressed. A group of researchers from the University of Michigan published a paper recently which details how they were able to break into the signal system, using only a laptop and an off-the-shelf radio transmitter, as reported in MIT Technology Review.
It was designed as a security test with the road agency’s permission, and unfortunately, the results demonstrated that signal infrastructure widely used across America (40 of 50 states) lacks sufficient security in today’s environment. The study uncovered three major weaknesses in the traffic light system: unencrypted wireless connections, the use of default usernames and passwords that could be found online, and a debugging port that is easy to attack. More technical details are available in the published report which was recently presented at a security conference.
Quoting from the report’s conclusion:
“With the appropriate hardware and a little effort, an adversary can reconfigure a traffic controller to suit her needs. She can execute a denial of service attack to cripple the flow of traffic in a city, cause congestion at intersections by modifying light timings, or even take control of the lights and give herself clear passage through intersections.”
(It’s nice to see that the University of Michigan is promoting gender equality!)